- CuttingEj
- Security Operations Centre
Security Operations Centre
Overview
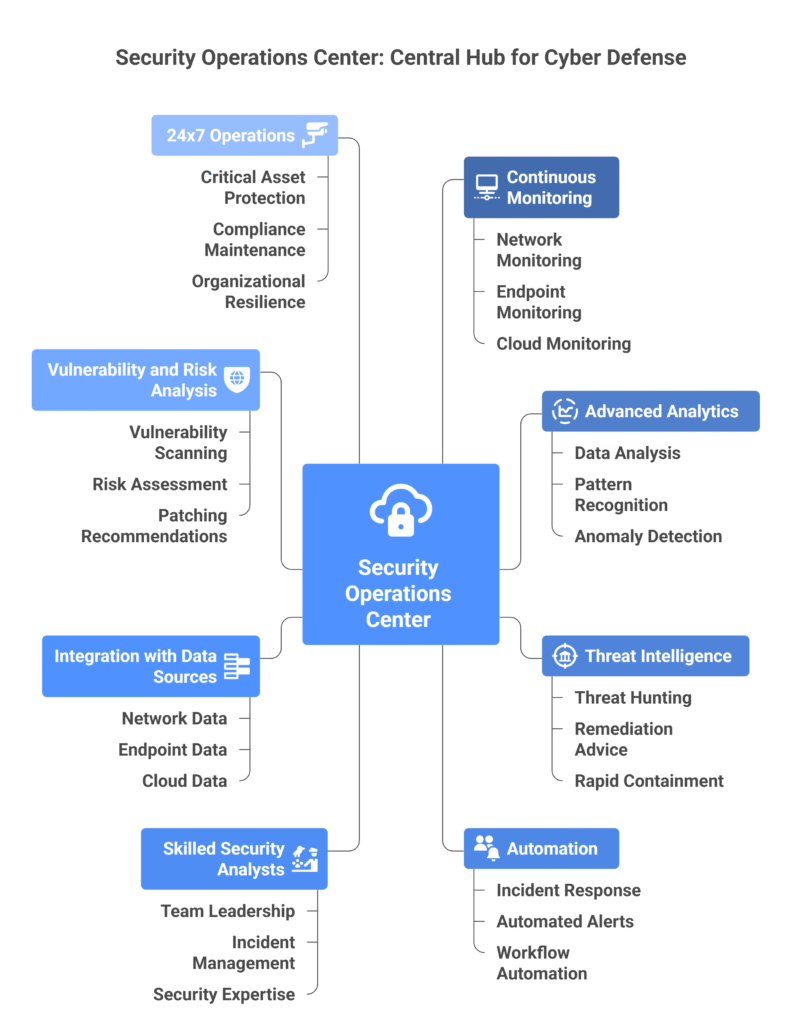
The cyber threat landscape is growing more perilous, with credible reports showing a staggering 70% rise in cloud incidents over the past year. How can you prepare for this escalating risk? Our Security Operations Center (SOC) serves as the command hub for continuous monitoring, analysis, and defense of enterprise systems against evolving cyber threats. It combines advanced analytics, threat intelligence, and automation to detect, investigate, and respond to potential incidents in real time. Led by skilled security analysts, the SOC proactively hunts for threats, advises technology teams on remediation actions, and ensures rapid containment of security events. Through integration with multiple data sources, it provides full visibility across networks, endpoints, and cloud environments. The SOC also conducts vulnerability and risk analysis, driving proactive recommendations for patching and system hardening. Designed around modern frameworks and best practices, it supports 24×7 operations to safeguard critical assets, maintain compliance, and strengthen organizational resilience
Business Problem
Emerging Cyber Attacks
Organization are witnessing more and more cyber and insider attacks in this digital world that is impacting their business
Threat actors are constantly upgrading their Tactics / Techniques / Procedures in performing cyber attacks
Insider threats are growing due to improper security configurations and controls
Lack of Visibility on Organization Threat Profile
Organizations are unable to measure their security posture as they don’t have complete visibility on their threat profile
Unidentified and untreated vulnerabilities and threats increase the attack surface and attack vectors
Limited SOC Skills
Organizations are lacking experienced resources in performing Real time monitoring of security alerts, Performing Incident management and proactive Threat hunting
Insufficient abilities cannot perform expert analysis on millions of logs / events, performing the triage and recommending accurate mitigation plans
Strict Regulations and Compliance
Inadequate visibility and control on vulnerabilities / threats / risks affects overall organization’s business / audit / legal / regulatory requirements and standards that they must comply with, such as ISO, NIST, HIPAA, GDPR, PCI, SOC2, etc
Not adhering to Security practices affect customer trust and may lose overall business
SOC Support Approach
Discovery
Kick-off call Document and verify the Pre-requisites Understand the Client Environment and Requirements Prepare the Project Plan Get access to Client environment
Security monitoring
24*7 real time security monitoring Perform Alert Triage Perform Threat Hunting exercises
Incident management
Create Incidents with relevant details Recommend the relevant countermeasures Identify Root Cause Analysis Follow-up with the owner till the closure
Advisory Services
Provides continuous guidance by analysing multi-source telemetry and advising on patching, hardening, and exposure reduction.
SOC Use-Cases
Real Time monitoring and Security Incident Management
Common use-cases are Reconnaissance, Lateral movements, Identity frauds, DOS / DDOS, Privilege escalations, Ransomware, etc.
Security Dashboards (Security Posture)
Incidents with mapping of MITRE ATT&CK framework for detailed information about threats TTP’s and required proactive measures to be considered
Analyze the security posture of organization network and way for improvements
Security Compliance
Dashboards and reports for tracking status of feasible and applicable controls
Threat Hunting and Advisory Services
Proactive recommendations on the IT services / tools / solutions being used
Identify false positive alerts and support in fine tuning the existing policies
Incident Management Process
Investigate the triggered alert that contains the details such as Rule applied, Log source, Hosts, Action, Message, etc. with in SLA and Response time (or) Perform Threat hunting exercises from ingested logs / events
Verify and validate any involved IOCs (IP / URL / Domain / Hash) from Online sources such as Virus Total / Cisco Talos / Threat Intelligence feeds to find its reputation
Collect more information from other security sources or internal security teams to analyze and finalize the alert is True / False positive
Alert Triage / Threat Hunting
This stage focuses on analyzing and verifying security alerts to determine if they represent real threats.
Investigate: Review alert details (rule, host, action, log source).
Validate IOCs: Check IPs, URLs, or hashes in threat intelligence sources like VirusTotal or Cisco Talos.
Correlate Data: Gather info from internal teams and logs to confirm if it’s a true or false positive.
Incident Creation
Raise an incident in ticketing tool with following details, if the triggered alert is analyzed as ‘True positive’
- Full details of the alert
- Incident Priority (Urgent * Impact)
- Analysis performed
- Evidences
- Recommendations
Closure
Follow-up with the owner till closure of the incident
Create a knowledge article that can be referred by security analysts for working on similar alerts in future
-
-
Locations: India and USA.
© All Copyright 2025 CuttingEj. All Rights Reserved. Redesigned by Sitesoch
