- CuttingEj
- Vulnerability Assessment and Penetration Testing
Vulnerability Assessment and Penetration Testing
Overview
Business Problem and Challenges
- Inadequate Security evaluations
Incomplete security evaluations leaves unidentified gaps, loopholes, misconfigurations in Network Infra / Security solutions / Servers and Applications such as Web / Mobile / APIs / Thickclients / Mobile / Payment Gateways that leads to Insider and Cyber Attacks
Inability to identify the attack surface and vectors increase the threat landscape and affect the overall organization security posture
- Lack of skilled resources
- Security Non-Compliance
VAPT Services
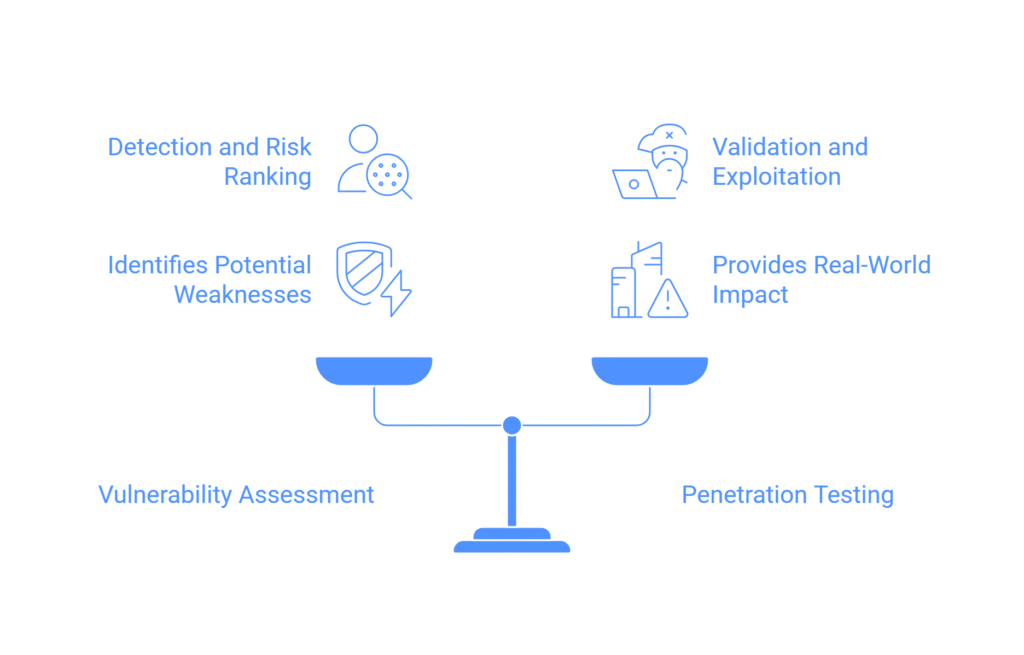
VAPT Use-Cases
Vulnerability Assessment
Vulnerability Assessments using automated tools and manual methods to find security gaps, loopholes, misconfigurations in Network Infra / Security solutions / Servers / Applications such as Web / Mobile / APIs / Thickclients / Mobile / Payment Gateways.
Assessment include checks on OS, Kernel, Apps installed, Libraries, software programs, packages, utilities, security misconfigurations, patching.
Exploit, Penetrate and Remediate
Non-intrusive Penetration testing using automated tools and manual methods to verify the identified vulnerabilities can be exploited and what impact it creates
Provides complete picture of existing security controls efficiency and effectiveness in detecting and preventing the simulated testings
Security Compliance
Organization’s business / audit / regulatory requirements to comply with Application security controls of various security frameworks / standards such as ISO, NIST, HIPAA, GDPR, PCI, SOC2, etc
Establish customer trust in generating or continuing the business
Scope and Business Benefits
Scope
- Network or Application hosted in On-Prem / Cloud
- Consideration of Security frameworks / standards / compliance checks according to requirements
- Automated scans and Manual testing’s
- White-box / Black-box testing’s
- Detailed recommendations/resolutions for all the findings
- Consulting and Support for fixing vulnerabilities
Benefits
- Prioritization of Resources
- Identification of Vulnerabilities and quantifying its impact
- Comply with Security and Regulatory Requirements
- Improved Security Posture
- Better Cost Savings
- Stay ahead of Threats and Risks
- Enhanced Customer Trust and Reputation
-
-
Locations: India and USA.
© All Copyright 2025 CuttingEj. All Rights Reserved. Redesigned by Sitesoch
